Sunday, July 27, 2008
Hackers control the internet traffic
"We are in a lot of trouble," said IOActive security specialist Dan Kaminsky, who stumbled upon the Domain Name System (DNS) vulnerability about six months ago and reached out to industry giants to collaborate on a solution.
"This attack is very good. This attack is being weaponised out in the field. Everyone needs to patch, please," Kaminsky said. "This is a big deal."
DNS is used by every computer that links to the Internet and works similar to a telephone system routing calls to proper numbers, in this case the online numerical addresses of websites.
The vulnerability allows "cache poisoning" attacks that tinker with data stored in computer memory caches that relay Internet traffic to its destination.
Attackers could use the vulnerability to route Internet users wherever the hackers wanted, no matter what website address is typed into a web browser.
The threat is greatest for business computers handling online traffic or hosting websites, according to security researchers. The flaw is a boon for "phishing" cons that involve leading people to imitation web pages of businesses such as bank or credit card companies to trick them into disclosing account numbers, passwords and other information.
"I was not intentionally seeking to cause anything that could break the Internet," Kaminsky said during a conference call with peers and media. "It’s a little weird to talk about it out loud."
Kaminsky built a webpage, www.doxpara.com, where people can find out whether their computers have the DNS vulnerability. As of Thursday, slightly more than half the computers tested at the website still needed to be patched. "People are spending tens of thousands of hours getting this patch out the door," Kaminsky said.
The US Computer Emergency Readiness Team (CERT), a joint government-private sector security partnership, is among the chorus urging people to quickly protect computers linked to the Internet. "Just like you should wear a seat belt going down the road to be safe in a car accident, the same applies here," said Jerry Dixon, a former director of cyber security at the US Department of Homeland Security.
Saturday, July 26, 2008
Beware, Renrou's watching you!
The search engine involves thousands of individuals, all mobilized to dig out facts and expose the baleful glare of publicity.
The Internet and conventional search engines are used for the purpose.
In 2001, a netizen posted the photo on Mop of a girl, claiming her to be his girlfriend.
However, Renrou helped other web users find out that woman was Microsoft's model Chen Ziyao, and her personal information was later used to expose that man.
A 41-year-old nurse named Wang Jue was suspended from her job when netizens using Renrou dug out her personal details while probing a video that showed her stabbing a kitten in the eyes with her high heels, and crushing its head.
There was observed a peak of Renrou searching when a husband whose wife committed suicide because of his betrayal, a man who disrupted torch relay in Paris and a girl from northeastern China who dared to criticize those affected by the massive earthquake became targets.
"Those who mistreated the vulnerable are likely to incur the hatred of netizens," Chinese news agency Xinhua quoted an online freelancer nicknamed Ayawawa, who herself was involved in a search for a disloyal husband, as saying.
"I just want them to be punished," she said, adding that according to Chinese law, such behaviour, although immoral, invite no legal punishment.
When a girl from a college in Chongqing municipality said on the Internet that the May 12 earthquake was "interesting", her mother and teacher started to receive threatening phone calls from angry netizens, forcing the girl to suspend her schooling.
The China Youth Daily recently surveyed 2,491 netizens, and found 79.9 per cent of them to believe that Renrou search should be regulated.
While 65.5 per cent thought it might become a new way of venting anger and revenge, 64.6 per cent said that it was infringing privacy, and 20.1 per cent feared that they could become a target.
Ayawawa also agreed that some targets were just scapegoats for netizens to vent their anger in daily life.
The survey also revealed that 24.8 per cent of those polled supported legislation to restrict Renrou searches.
Tuesday, June 24, 2008
New FRAUD Strategies - Keyboard
CHECK THE BACK OF THE PC AND SEE IF THE BELOW DEVICE IS THERE..IF SO..DO NOT USE IT!!!!
 New storing device fits at the end of the keyboard cable connecting to the PC specialized to save all typed keys in it…
New storing device fits at the end of the keyboard cable connecting to the PC specialized to save all typed keys in it…Mostly could be used in net cafes, exhibitions, hotels and airports therefore be careful especially the people who use the internet in these places to enter their bank accounts online or any other important sites.
After you enter the bank account and leave the PC it will be easy to open your account again as all what you have typed has been saved in the Black device.
Therefore, you should check the PC for any suspicious piece behind it before using the net in public places for important sites.
Saturday, June 21, 2008
How to access your PC remotely
When you're visiting friends far from home, for example, but forgot to transfer the promised vacation photos onto your laptop, gaining access to your PC can be invaluable.
Several Windows versions offer remote access through the Remote Desktop function. But, there are also stand-alone programmes allowing PCs to be controlled from any browser.
This latter category includes VNC (Virtual Network Computing Protocol) and the variants based upon on it. The most recent version of VNC sends a small programme onto the other computer, known as a client or remote computer, which is used to control the home PC.
The client's browser then displays a view of the desktop back at home and with it full access to the PC. That said, access via browser is more sluggish than if the VNC software is also installed on the client machine.
During installation it must be indicated whether the PC being used is a client or server PC. For security reasons the access password should be set on the server PC.
The user must also ensure that the software will not be blocked by a firewall.
Internet service providers generally assign their customers a new IP address for each new online session. To make remote control possible, a so-called dynamic DNS service must be employed.
Many routers come ready-made for services like DynDNS. The ISP provides the user with a domain name, including information on host, user name, and password, to enter into the router. The base service is generally free.
During a comparison of several VNC variants, Munich-based PC Professionell magazine found UltraVNC to be the best. The software is available for Windows and Linux. The chat options provided by the software as well as the simple exchange of files and folders are calling cards of the cost-free software.
CSpace is also available as a no-cost remote software option. The software must be installed on the Client PC, and only works with Windows and Linux.
It does not offer browser support. Remote control then works without configuration -- even through routers and firewalls and without port forwarding. One of several cost-free VNC client programmes for Mac OS X is Chicken of the VNC. Microsoft primarily worked its Remote Desktop service, including remote control and remote servicing, into the pro versions of its operating systems. "Where available, Remote Desktop is without question the best choice for remote control of current Windows systems," Hanover-based c't magazine found. It is quick, convenient, and seamlessly integrated into the system. |
Friday, June 13, 2008
How to keep tabs on your Net addiction?
 Almost everyone who logs on to the internet these days claims some level of internet addiction. Be it addiction of constantly checking emails, reading news sites or some mindless surfing. PageAddict (pageaddict.com) is one tool that will let you keep your internet addiction. The application sits on your Firefox explorer as an add-on extension. Once installed it gives you a detailed category wise summary of the time you’ve wasted on each web site. And there is even an option to restrict how much time you spend in each category in a day.
Almost everyone who logs on to the internet these days claims some level of internet addiction. Be it addiction of constantly checking emails, reading news sites or some mindless surfing. PageAddict (pageaddict.com) is one tool that will let you keep your internet addiction. The application sits on your Firefox explorer as an add-on extension. Once installed it gives you a detailed category wise summary of the time you’ve wasted on each web site. And there is even an option to restrict how much time you spend in each category in a day.
Thursday, June 12, 2008
What's making you angry?

It’s common to read in newspaper stories about a usually calm and intelligent person who “snaps” and commits a violent act.
Some people lose their tempers in this way, repeatedly and dramatically, causing serious physical harm to others. It’s a pattern in which tension builds until an explosion brings relief, followed eventually by regret, embarrassment, or guilt feelings.
In this sudden outburst, people might do things they normally would not even think of doing —they might break things, abuse others, hurt or try to hurt someone else or even try to harm themselves. The degree of aggressiveness expressed during the episodes is grossly out of proportion to any precipitating psychosocial stressors. Yes, we are talking about a disorder called Intermittent Explosive Disorder.
What is intermittent explosive disorder?
On the way to work, you hurl abuses at the driver who just cut you off. At the office, a trivial problem gets your blood pressure high. That night at home, you fight with your spouse and throw a bottle of water against the wall.We all have a propensity to get angry and upset. But then, there are people who react to situations with a sudden outburst without thinking about repercussions. This little-known disorder marked by episodes of unwarranted anger is more common than previously thought, a study funded by the National Institutes of Health’s (NIH) has found. Intermittent explosive disorder (IED) affects as many as 7.3 percent of adults in their lifetime.
Why people suffer from IED
Research findings suggest that IED may result from abnormalities in the areas of the brain that regulate behavioural arousal and inhibition. Impulsive aggression is related to abnormal brain mechanisms in a system. Persons with IED have a set of negative beliefs strongly embedded in their personality, often resulting from harsh punitive methods inflicted by the parents. The child grows up believing that others “have it in for him” and that displaying anger is the best way to restore damaged self-esteem. There is some evidence of that the neurotransmitter serotonin may play a role in this disorder.
Symptoms of IED
Many people diagnosed with IED appear to have general problems with anger or other impulsive behaviors. They may experience racing thoughts or a heightened energy level during the aggressive episode, with fatigue and depression developing shortly afterward. Some report various physical sensations, including tightness in the chest, tingling sensations, tremor, or a feeling of pressure inside the head.
Diagnosis
A psychologist who is evaluating a patient for IED would first take a complete case history. One has to rule out head trauma, epilepsy, and other general medical conditions that may cause violent behavior. Series of psychological tests are conducted to rule out other personality disorders.
Treatment
Anger management skills through a combination of cognitive restructuring, raising endurance levels, and relaxation training looks promising. And because intermittent explosive disorder often begins in early adolescence, parents need to be vigilant in tapping aggressive symptoms in their teens. Treatment could involve medication, with the best prognosis utilising a combination of the two.
Some Tips
Better communication : Angry people tend to jump to and act on conclusions and some of those conclusions can be very inaccurate. The first thing to do if you're in a heated discussion is slow down and think through your responses.
Get away from the situation : Sometimes our immediate surroundings give us cause for irritation and fury. Problems and responsibilities can weigh on you and make you feel "trapped"; making you resentful." Give yourself a break.
Be tolerant : All you have to do to practice tolerance, accept other people as they are, not as you would like them
to be. When you are tolerant, your actions will almost always become more logical and reasonable.
Ralph Waldo Emerson wrote, “For every minute you are angry you lose sixty seconds of happiness.”
Sunday, May 25, 2008
7 tips for keeping kids safe online

Any parent who has spent a few minutes trying to decipher the abbreviations in his or her teenager’s online chat conversations knows that the web hosts a youth culture all its own. And that world doesn’t just have its own language, it also fosters the sharing of personal information among friends—and sometimes strangers—that can set off alarm bells for parents. Here are a few tips for keeping up with your kid in this quickly evolving space—and helping to draw the line between harmless socializing and dangerous breaches of privacy
1. Talk to your kids about the web:
More important than trying to limit or control your kids’ web access is to educate them about what information-sharing and behaviour is smart and responsible on the net. Make it clear to your kids that everything they post to a social networking site, or even send in an email, could easily end up being widely distributed to anyone in cyberspace—including people they’d never talk with in person. On the list of details they should never share online: home addresses, phone numbers, any financial information, sensitive personal details or compromising pictures.
2. Use kid-oriented social networks:
One easy way to limit the dangers of social networking is to sign up your preteen kids for social networking sites designed for safety. The social network Imbee.com, for instance, is built to replicate real world friendships online, not to help kids meet strangers. Users can only access profiles within a limited network of friends. All new connections are approved by parents. The kids’ networking site Club Penguin is even safer, albeit targeted at a very young audience—with certain settings, users can only chat using a set of harmless phrases.
3. Use content-locking tools sparingly:
Programs like Net Nanny or Cybersitter can block objectionable content on the web and make tracking your children’s online behaviour easy. But Larry Magid, founder of Safekids.com and Connectsafely.org, suggests parents think twice before locking down internet use with these kinds of programs. For teenagers, these sorts of software are likely to inspire rebellion and tempt them to find other, less censored paths to blocked material. For younger kids, Magid suggests the filters are often a poor substitute for more long-lasting education about online safety.
4. Agree on good terms for web use:
The internet is more widely accessible every day, so a kid given strict rules about online behaviour without his or her input is likely to find a less restrictive entryway to the web. Instead, come to an agreement with your kids about what you both consider acceptable behaviour in terms of balancing their privacy and their safety. Larry Magid suggests parents and children write and sign pledges for proper online behaviour and post them by the family computer.
5. Monitor Your Kids’ Online Profile:
One of the dangers of social networking and blogging is that so much of it occurs on the public web, where it’s broadcast to the world. But if strangers can access kids’ profiles and blogs, so can parents. Just as you stay involved in your child’s friendships in the offline world, you can also keep tabs on his or her online socializing, either actively participating for younger kids or watching from a less intrusive distance for teenagers.
6. Pick your location for computer carefully:
Setting up a desktop computer that’s tied to a certain location in the house, rather than buying a laptop and using a wireless internet connection, is one way to make keeping an eye on your child’s web use easier. Even better: Put that computer in a high-traffic area of the house, like the living room or family room, to ensure that web surfing stays public. Keeping the internet out of your child’s bedroom also helps you balance his or her online activity with a healthy mix of offline activities like sports and reading.
7. Monitor cellphone use:
As phones get smarter, the line between a cellphone and a net-connected computer is beginning to blur. If your child has a phone with internet capabilities, you should be sure to include cellphone use in your discussion about safe online communication. Monitoring your phone bill is one way to keep tabs on the amount of web browsing your child is doing over a cellular network.
Sunday, May 11, 2008
Tips to recover scratched CD/DVDs
Read-on, if you find yourself wishing for a miracle every time your fav CD is scratched:
Home Remedy :
here's an easy home remedy, which might give you the desired results. Rub a small amount of toothpaste on the scratch and polish the CD with a soft cloth and any petroleum-based polishing solution (like clear shoe polish). Squirt a drop of Brasso and wipe it with a clean cloth.
Technology to the rescue
There are many softwares available on the net, which enable the recovery of the CD data. BadCopy Pro is one such software, which can be used to recover destroyed data and files from a range of media.
Just a few clicks is all it requires to recover the disc from almost all kind of damage situation; be it corrupted, lost data, unreadable or defective. DiskDoctors is another popular company, which offers both software and solutions to recover data from a scratched CDs and DVDs.
General Tips:
* Always wipe the CD from the center outward with stratight spoke-like strokes. Wiping CDs in circles will create more scratches.
* Do not scratch the graphics layer as you cannot repair the disc. HINT: Hold the disc up to a light with the graphics layer facing the light source. If you can see light thru the scratches at any point then the disc may be irreparable and or exhibit loading or playing errors.
* Clean your Disc players lens regularly with a suitable product to ensure optimal viewing pleasure.
* Make sure to use a soft, lint-free cloth to clean both sides of the disc. Wipe in a straight line from the centre of the disc to the outer edge.
* If wiping with a cloth does not remove a fingerprint or smudge, use a specialized DVD disc polishing spray to clean the disc.
* Only handle the disc by its outer edge and the empty hole in the middle. This will help prevent fingerprints, smudges or scratches.
Statistics:
*Fingermarks/ prints cause 43% of disc problems!
* General wear & tear causes 25% of disc problems!
* Player-related issues cause 15% of disc problems!
* User-related issues cause 12% of disc problems!
* PlayStation 2 machine scratches cause 3% of disc problems!
* Laser rot (a manufacturer error) causes 2% of disc problems!
Saturday, April 19, 2008
Amazing Magic For those of you using Windows
An Indian discovered that nobody can create a FOLDER
anywhere on the computer which can be named as 'CON'.
This is something pretty cool...and unbelievable.
At Microsoft the whole Team, couldn't answer why this
happened!
TRY IT NOW ,IT WILL NOT CREATE ' CON ' FOLDER
MAGIC # 2
For those of you using Windows, do the following:
1.) Open an empty notepad file
2.) Type "Bush hid the facts" (without the quotes)
3.) Save it as whatever you want.
4.) Close it, and re-open it.
is it just a really weird bug? :-??
MAGIC # 3
microsoft crazy facts
This is something pretty cool and neat...and unbelievable... At Microsoft the whole Team, including Bill Gates, couldn't answer why this happened!
It was discovered by a Brazilian. Try it out yourself...
Open Microsoft Word and type
=rand (200, 99)
And then press ENTER
then see the magic...............................
It is Working & it is tested by me & no harm to the PC in any Form!
Sunday, April 13, 2008
Thursday, March 06, 2008
How To Make Windows XP Genuine
Method 1:
1)The process involves in changing key of your current Xp.
2)For that you have download the key changer from
http://rapidshare.com/files/90596417/Key_Changer.rar.html
3)After running the key finder You will find this dialog box
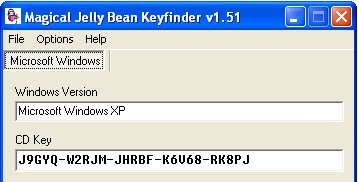 4) I f you click Option menu you see the following click on the Change Windows Key
4) I f you click Option menu you see the following click on the Change Windows Key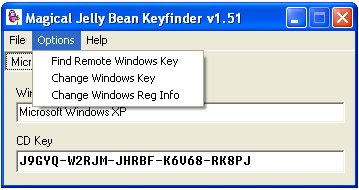 5)you will get the following dialog box
5)you will get the following dialog box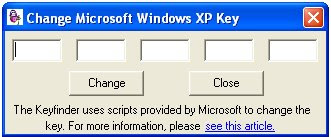
In this dialog box type the following key and click OK
"V2C47-MK7JD-3R89F-D2KXW-VPK3J"
Now your windows Xp is made genuine.
4)Now you can install IE 7.0, WMP 11 and many more. Enjoy Genuine Xp. You can solve the generic host services problem also..
This method surely works.
Method 2:
To crack the Windows XP make the XP genuine download the following link
Click to Download
After downloading run the exe to crack
Windows Vista Crack:
To crack the Windows vista make the vista genuine download the following link
Click to Download
After downloading run the exe to crack
Tuesday, February 26, 2008
how a computer works? ... It makes so much sense
The safe way to abandon your PC
Here is how to do that, in a safe and secure way
Wednesday, December 12, 2007
10 Things Your iPod Won't Tell You

1. "It's good to be king — but my reign may be coming to an end."
Since launching the iPod in 2001, Apple has been the undisputed leader in digital music players, owning 90 percent of the market. What has set the iPod apart is not only its hip, user-friendly design, but also its companion iTunes music store, the first online audio megamart, offering an ever-expanding catalog of songs for purchase at the click of a mouse. This two-pronged approach has given Apple a huge lead over competitors; so far the company has sold over 40 million iPods and more than a billion songs on iTunes. But the iPod's days at the top may be numbered.
At issue is Apple's proprietary format, which makes the iPod incompatible with other digital-music technology. According to Chris Crotty, senior analyst for consumer electronics at iSuppli, such closed systems either move toward compatibility or get surpassed by the competition. Think of AOL's early bid to set up its own online world — highly successful, until the bigger and better Internet rendered it obsolete. Apple is similarly positioned and could end up painting itself into a corner, just as it did with Macintosh. "Over time the market prefers open systems," Crotty says.
2. "Customer service is a privilege, not a right."
Customer Service isn't what it used to be. According to Ross Rubin, analyst at the NPD Group, companies across the board are pushing "more self-service" to cut costs. But even so, he says, Apple is "pretty aggressive in terms of the consumer electronics industry." IPod buyers, for example, get just one call to customer service during the first 90 days of ownership; each one after that costs $49. (If you want more phone time, the AppleCare Protection Plan costs $59, offers unlimited calls for two years and doubles the one-year warranty.)
3. "If you drop me, I'm toast."
You've seen the ads — hip, young people exuberantly dancing with iPod in hand. But the reality is, the device is delicate. Apple's edgy designs "tend to be more attractive, but also more fragile" than other players, says industry analyst Rob Enderle.
At the heart of many iPods is a tiny hard drive that can stop working if it's dropped or even knocked around. (Just imagine boogying down the sidewalk with your laptop.) But it's not only the hard drive that needs careful handling — the screens on these players have been a source of trouble as well. Apple admits some of its Nano iPod screens were faulty, causing them to crack and scratch too easily, but claims the problem affected "less than 1 percent." Patrick Destvet, a New York City psychologist, says it isn't just a Nano problem; the color screen on his new 30-gigabyte video iPod was scratched up after a month, making it hard to see anything on the device. "Coming from Apple, I didn't expect this," Destvet says.
To protect your iPod, invest in a padded case. Apple sells a $99 leather shell; other good covers include Incase's neoprene sleeves and Speck Products' rubberized cases. Visit www.applestore.com for the best selection.
4. "You say 'backup'; we say 'copyright infringement.'"
Apple makes it very easy to load your iPod with music — iTunes software is free to anybody who wants it. But once you've filled your player with as many as 15,000 songs, it's not so easy to get them off again. Because of copyright issues, Apple doesn't let you move music from your iPod to another computer or other electronic devices, even though it would be legal to do so. This measure was taken to appease the music companies. "A lot of people are quick to point the finger, but it's not Apple that is necessarily driving the restrictions," Crotty says. "Not that they mind" — since such controlsallow Apple to stymie the competition.
Fortunately, there are ways to circumvent Apple's roadblock through third-party software, which allows you to move music from your iPod back to any computer. Among the many options, both Mac and PC users can download PodUtil (about $20) from www.kennettnet.co.uk, while PC users can save a few bucks with PodPlus ($15), available at www.ipodsoft.com. After downloading the software, you'll be asked to plug in your iPod so the software can pull the music from your player and save it in your iTunes folder.
5. "My battery life is pathetic."
The new iPod boasts a robust battery life of 20 hours. But if you look at the fine print, Apple admits on its Web site that "battery life and number of charge cycles vary by use and settings." The company also warns consumers that you can recharge a battery only so many times before it must be replaced. According to The Rough Guide to iPods, the magic number is 500, depending on use. And you'll know it's coming — after 400 charges, your iPod's battery will hold only about 80 percent of its capacity.
For a few years Apple simply refused to recognize the problem and recommended that users buy a new player if the battery died. Only after a public outcry — and a class-action lawsuit — did the company develop a battery-replacement program. Now you can send back your ailing iPod and get another for $59, plus $6.95 shipping. Most likely, you'll receive a comparable used or refurbished unit.
Better to extend the life of the battery you have. Do this by regularly updating your iPod's software. Check Apple's Web site for the latest version; you can download a free upgrade there. And don't charge your iPod in its case, where it can overheat and diminish the battery's capacity.
6. "I'm destroying your hearing."
A major selling point of digital music players is that you can tune out the world around you for hours at a time. But as you crank up your iPod to drown out ambient noise, you could be damaging your ears. According to a study by the American Speech-Language-Hearing Association, at full volume an iPod can generate up to 120 decibels, equal to the sound of a jet plane taking off. At that level you'll begin sustaining permanent hearing loss or tinnitus after just five to 10 minutes. The issue is serious enough that Apple recently introduced software that allows you to cap the volume of your iPod, or your child's iPod (available for free download at the Apple Web site). "Noise-induced hearing loss is easy to ignore until it's too late," says Pam Mason, an audiologist at the ASLHA. Extended listening at 80 to 85 decibels is safe, according to Mason. Roughly speaking, that means you should turn it down if you can't hear someone talking normally three feet away from you or if the people around you can hear your music. It also helps to invest in a good pair of noise-canceling or noise-isolating earphones. Both types block out ambient sound so you needn't jack up the volume as high. 7. "I'm out of date before I'm out of the box." Last fall small-business owner Peter Quinones wanted to replace his iPod but kept hearing Apple was about to come out with an improved model. "I was in a holding pattern," the Miami resident says. "You don't want to buy something and find out a week later there's a new product." So Quinones waited six months, then bought a video iPod instead of the Nano he'd been considering. His new player worked with the cradle in his Mercedes; the Nano wouldn't have. All consumer tech companies have shortened their product cycles, adding innovative new features to maintain their competitive edge. But with the iPod, Apple seems to be churning out new versions at an unprecedented rate: In just the past 14 months, the company has introduced 12 models. By contrast, the first 14 iPod models were rolled out over the course of three years. "It can be a nuisance for some consumers," says Susan Kevorkian, an analyst at IDC, since some of the older accessories, such as speakers or docks, aren't necessarily compatible with the newer models. Fortunately, Apple has now standardized the docks for the iPod, meaning future models should still work with the one you buy today. 8. "I've sparked a crime wave." You know a product is popular when it becomes a favorite target of thieves. In New York City, an increase in crime on the subways has been blamed on the iPod, as folks sporting the telltale white earphones are being ripped off in record numbers. And sadly, 15-year-old Christopher Rose was killed last summer in Brooklyn when he refused to hand over an iPod to a mugger. But iPod crime isn't isolated to urban areas. A number of college and high school campuses have experienced a rash of thefts, leading some schools to ban the device. Keith Bromery, spokesperson for the Broward County school board in Florida, says that district recently restricted the use of iPods and other electronic devices, citing theft and peer pressure to own these items as distractions to learning. Kevin H. Watson, spokesperson for the Law Enforcement Alliance of America, says the iPod is a favorite among thieves because "it's easy to conceal, it has turnover value on the street and people are willing to buy one on the black market." Not to mention, they're easy to spot: "The white headphones are a giveaway," he says, "just like flashing a fancy watch." He recommends other earphones and not using your iPod in dicey areas. 9. "We'll nickel-and-dime you any chance we get." The first quarter of this year was a record-breaker for Apple: The company reported new highs for both revenue ($5.75 billion) and earnings ($565 million). Yet even with these impressive financial stats, the company continues to pile on extra fees for owning and maintaining an iPod. We're not talking about the burgeoning iPod accessories market, such as stylish cases and portable speaker systems. No, Apple has begun charging for standard equipment it once included with the cost of the player. Why? "It keeps retail prices down and drives sales volume," Kevorkian says. Early iPod models shipped with a wall charger and a dock. These "extras" will now cost you $29 and $39, respectively. Want to connect your video iPod to a TV? You'll have to buy a cord separately, for $19. Adding insult to injury, should your iPod conk out after the warranty expires, you could end up paying more to get it fixed than it would cost to buy a new one — repairs on a Nano, for example, run a standard $189 plus shipping, while new in the box, it's as little as $150. 10. "Once you go iPod, you're locked in for life." One of the reasons Apple has been able to dominate the digital music player market until now is that while the iPod can play songs from a variety of sources, music bought online at the iTunes store can be used only on an iPod. That's because the company developed its own format for songs, called Protected AAC, instead of using the widely compatible MP3. Crotty points out that while basic AAC is an open format, the digital rights management software Apple lays over it — called, ahem, "Fair Play" — renders it incompatible with other players. No other company is legally allowed to make a device that can play songs in Apple's format. The company claims AAC has many advantages over MP3, but the format also serves as the lock on the iPod's closed door — which could lead to its downfall. "They've set themselves up as Apple and the iPod versus the rest of the MP3 market," Crotty says. "Customers may get upset that they can't move their purchased music." The tide is already turning in Europe, which, he adds, "doesn't accept a closed system as a business practice": The French government is considering a law that would force Apple to allow music on the iTunes store to work on competitors' players.
Tuesday, December 11, 2007
10 Simple Tips for Using Email

We all use email but, sometimes we use it too much or use it inappropriately. To get the most out of email we need to use it carefully and judiciously. These are 10 tips to get the most out of emailing.
1. Use different email accounts for different purposes.
It is is good to have separate email accounts for separate purposes. For example, you may have one for business and one for social activities. This means you can check the personal email in the evening without having to think / worry about business. If you see an important message from your boss it could ruin your weekend or evening. At the end of the day you want to be able to get away from work. Don’t allow email to make you a slave to work. Some people feel it is inconvenient to check 2 different email accounts. But the relative inconvenience is easily outweighed by the benefits.
2. Email is not always the best Form of contact.
If you have a really important issue or you are upset with someone, emailing is often not the best answer. If necessary speak to the person directly, rather than through an email.
3. Don’t say anything you wouldn’t say in person.
This advice has certainly been given before. But, it is always worth reminding ourselves about the importance of being polite and avoiding unnecessary rudeness. We will regret it later. Email makes it easier to use harsh words because it is impersonal. We need to be very careful.
4. Use a Good Title
Many people ignore the title of an email. If the subject changes don’t keep using an old “re:irrelevant title” A good title increases the chance that people will actually read your email, rather than just leaving it for later. A bad title may even get deleted as spam.
5. Don’t Ignore Basics of English.
Just because it is an email, doesn’t mean we have to write like a 5 year old or use text message language. This indicates laziness and a lack of care. If you haven’t time to respond properly, wait until you do. Keep emails brief, but don’t completely ignore the basic use of grammar and spelling.
6. Keep it Short
Emails can be brief and to the point. If the message has to be long, make sure it is broken up in to different sections, which are easy to read. But, generally you should aim to keep it less that 5 sentences. This is good for both the writer and the reader.
7. Acknowledge Important Emails.
If somebody sends some important documents, files or message, make sure you, at least, acknowledge their receipt. Otherwise they may be uncertain that they got them. It doesn’t have to be long; it can be quite short.
8. Create a Standard Responses
If you find yourself sending similar answers to many people, compose a draft message and save it in your drafts folder (or write it in word). You can use this standard response for emailing many people. Don’t forget to personalise it by adding their name.
9. Be careful about Replying To All.
If you are new to email make sure you know the difference between replying to one person and replying to everyone on the initial message. Suffice to say you will send many emails which you would not want to be seen by everyone. It can be extremely embarrassing to send a personal message for everyone to see - it does happen. If you have new workers, make sure they are aware of this distinction. It will save a lot of potential problems.
10. Compose Your Signature.
Having a signature looks professional and saves typing the same information every email. Remember people may wish to contact you through over methods than email. So make sure you have a phone number and address. If relevant add any qualifications and websites that you have. This gives people a chance to find out more about you.
Saturday, November 10, 2007
Make a CD Protector

Tuesday, November 06, 2007
How to Enable the Windows Task Manager?
As a system administrator you can manage all the features of Windows Task Manager.
You can end task of any running application and set the priority of any running process according to application importance.
By default Windows Task Manager Status is enabled, but a user can also disable or enable it manually.
But sometimes a registry hack applies on windows task manager to disable it and your system give you a message "Task Manager has been disabled by your administrator”.
Then you should enable it by editing the system registry or using Group Policy Editor.
Before proceeding further, first scan your system with up-to-date antivirus, and then follow the given steps to enable it using group policy editor.

-
To enable this feature, you will need to be logged into your computer with administrative rights.
-
Now click on Start button and type “Gpedit.msc” in Run option then press OK.

-
In Group Policy Editor, expand "User Configuration",> expand the “Administrative Templates”,> expand “System” then “Ctrl+Alt+Del Options”,
-
Now in right side of panel “Ctrl+Alt+Del Options” double click on “Remove Task Manager” to change it setting. Here set the option “Disable” to “Enable” or “Not configured” and your task manager is available once again.

How to speed up your Broadband internet connection?
By enabling these setting, you can use this reserve bandwidth and enjoy your speedy broadband internet connection. You can set reserve able limit from 0 to 100 percent, but if you want to enjoy 100 percent bandwidth of internet connection, you should configure bandwidth limit 0 percent.
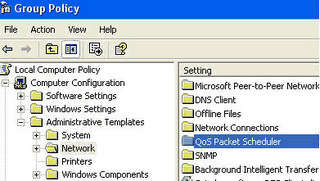
- First click on Start button then type "GPedit.msc" in Run option and press Enter.
- Under "Local Computer Policy" expand the "administrative templates".
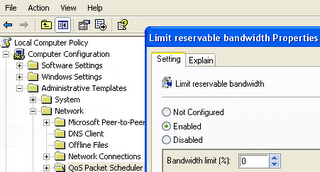
- Here in left side window expand the "Network" then highlight the "QoS Packet Scheduler".
- Now again in right side window, double click on "limit reservable bandwidth".
- Under the "Limit reservable bandwidth properties" dialog box check "enabled" then change the "Bandwidth limit % to zero.
- Now close the Group Policy editor and restart your compute, after any changes to get into effect.
101 Shotcut keys for Windows
CTRL+X (Cut)
CTRL+V (Paste)
CTRL+Z (Undo)
DELETE (Delete)
SHIFT+DELETE (Delete the selected item permanently without placing the item in the Recycle Bin)
CTRL while dragging an item (Copy the selected item)
CTRL+SHIFT while dragging an item (Create a shortcut to the selected item)
F2 key (Rename the selected item)
CTRL+RIGHT ARROW (Move the insertion point to the beginning of the next word)
CTRL+LEFT ARROW (Move the insertion point to the beginning of the previous word)
CTRL+DOWN ARROW (Move the insertion point to the beginning of the next paragraph)
CTRL+UP ARROW (Move the insertion point to the beginning of the previous paragraph)
CTRL+SHIFT with any of the arrow keys (Highlight a block of text)
SHIFT with any of the arrow keys (Select more than one item in a window or on the desktop, or select text in a document)
CTRL+A (Select all)
F3key (Search for a file or a folder)
ALT+ENTER (View the properties for the selected item)
ALT+F4 (Close the active item, or quit the active program)
ALT+ENTER (Display the properties of the selected object)
ALT+SPACEBAR (Open the shortcut menu for the active window)
CTRL+F4 (Close the active document in programs that enable you to have multiple documents open simultaneously)
ALT+TAB (Switch between the open items)
ALT+ESC (Cycle through items in the order that they had been opened)
F6 key (Cycle through the screen elements in a window or on the desktop)
F4 key (Display the Address bar list in My Computer or Windows Explorer)
SHIFT+F10 (Display the shortcut menu for the selected item)
ALT+SPACEBAR (Display the System menu for the active window)
CTRL+ESC (Display the Start menu)
ALT+Underlined letter in a menu name (Display the corresponding menu)
Underlined letter in a command name on an open menu (Perform the corresponding command)
F10 key (Activate the menu bar in the active program)
RIGHT ARROW (Open the next menu to the right, or open a submenu)
LEFT ARROW (Open the next menu to the left, or close a submenu)
F5 key (Update the active window)
BACKSPACE (View the folder one level up in My Computer or Windows Explorer)
ESC (Cancel the current task)
SHIFT when you insert a CD-ROM into the CD-ROM drive (Prevent the CD-ROM from automatically playing)
Dialog Box Keyboard Shortcuts
CTRL+TAB (Move forward through the tabs)
CTRL+SHIFT+TAB (Move backward through the tabs)
TAB (Move forward through the options)
SHIFT+TAB (Move backward through the options)
ALT+Underlined letter (Perform the corresponding command or select the corresponding option)
ENTER (Perform the command for the active option or button)
SPACEBAR (Select or clear the check box if the active option is a check box)
Arrow keys (Select a button if the active option is a group of option buttons)
F1 key (Display Help)
F4 key (Display the items in the active list)
BACKSPACE (Open a folder one level up if a folder is selected in the Save As or Open dialog box)
m*cro$oft Natural Keyboard Shortcuts
Windows Logo (Display or hide the Start menu)
Windows Logo+BREAK (Display the System Properties dialog box)
Windows Logo+D (Display the desktop)
Windows Logo+M (Minimize all of the windows)
Windows Logo+SHIFT+M (Restore the minimized windows)
Windows Logo+E (Open My Computer)
Windows Logo+F (Search for a file or a folder)
CTRL+Windows Logo+F (Search for computers)
Windows Logo+F1 (Display Windows Help)
Windows Logo+ L (Lock the keyboard)
Windows Logo+R (Open the Run dialog box)
Windows Logo+U (Open Utility Manager)
Accessibility Keyboard Shortcuts
Right SHIFT for eight seconds (Switch FilterKeys either on or off)
Left ALT+left SHIFT+PRINT SCREEN (Switch High Contrast either on or off)
Left ALT+left SHIFT+NUM LOCK (Switch the MouseKeys either on or off)
SHIFT five times (Switch the StickyKeys either on or off)
NUM LOCK for five seconds (Switch the ToggleKeys either on or off)
Windows Logo +U (Open Utility Manager)
Windows Explorer Keyboard Shortcuts
END (Display the bottom of the active window)
HOME (Display the top of the active window)
NUM LOCK+Asterisk sign (*) (Display all of the subfolders that are under the selected folder)
NUM LOCK+Plus sign (+) (Display the contents of the selected folder)
NUM LOCK+Minus sign (-) (Collapse the selected folder)
LEFT ARROW (Collapse the current selection if it is expanded, or select the parent folder)
RIGHT ARROW (Display the current selection if it is collapsed, or select the first subfolder)
Shortcut Keys for Character Map
After you double-click a character on the grid of characters, you can move through the grid by using the keyboard shortcuts:
RIGHT ARROW (Move to the right or to the beginning of the next line)
LEFT ARROW (Move to the left or to the end of the previous line)
UP ARROW (Move up one row)
DOWN ARROW (Move down one row)
PAGE UP (Move up one screen at a time)
PAGE DOWN (Move down one screen at a time)
HOME (Move to the beginning of the line)
END (Move to the end of the line)
CTRL+HOME (Move to the first character)
CTRL+END (Move to the last character)
SPACEBAR (Switch between Enlarged and Normal mode when a character is selected)
m*cro$oft Management Console (MMC) Main Window Keyboard Shortcuts
CTRL+O (Open a saved console)
CTRL+N (Open a new console)
CTRL+S (Save the open console)
CTRL+M (Add or remove a console item)
CTRL+W (Open a new window)
F5 key (Update the content of all console windows)
ALT+SPACEBAR (Display the MMC window menu)
ALT+F4 (Close the console)
ALT+A (Display the Action menu)
ALT+V (Display the View menu)
ALT+F (Display the File menu)
ALT+O (Display the Favorites menu)
MMC Console Window Keyboard Shortcuts
CTRL+P (Print the current page or active pane)
ALT+Minus sign (-) (Display the window menu for the active console window)
SHIFT+F10 (Display the Action shortcut menu for the selected item)
F1 key (Open the Help topic, if any, for the selected item)
F5 key (Update the content of all console windows)
CTRL+F10 (Maximize the active console window)
CTRL+F5 (Restore the active console window)
ALT+ENTER (Display the Properties dialog box, if any, for the selected item)
F2 key (Rename the selected item)
CTRL+F4 (Close the active console window. When a console has only one console window, this shortcut closes the console)
Remote Desktop Connection Navigation
CTRL+ALT+END (Open the m*cro$oft Windows NT Security dialog box)
ALT+PAGE UP (Switch between programs from left to right)
ALT+PAGE DOWN (Switch between programs from right to left)
ALT+INSERT (Cycle through the programs in most recently used order)
ALT+HOME (Display the Start menu)
CTRL+ALT+BREAK (Switch the client computer between a window and a full screen)
ALT+DELETE (Display the Windows menu)
CTRL+ALT+Minus sign (-) (Place a snapshot of the active window in the client on the Terminal server clipboard and provide the same functionality as pressing PRINT SCREEN on a local computer.)
CTRL+ALT+Plus sign (+) (Place a snapshot of the entire client window area on the Terminal server clipboard and provide the same functionality as pressing ALT+PRINT SCREEN on a local computer.)
m*cro$oft Internet Explorer Navigation
CTRL+B (Open the Organize Favorites dialog box)
CTRL+E (Open the Search bar)
CTRL+F (Start the Find utility)
CTRL+H (Open the History bar)
CTRL+I (Open the Favorites bar)
CTRL+L (Open the Open dialog box)
CTRL+N (Start another instance of the browser with the same Web address)
CTRL+O (Open the Open dialog box, the same as CTRL+L)
CTRL+P (Open the Print dialog box)
CTRL+R (Update the current Web page)
CTRL+W (Close the current window)
Last But not Least.
My Most Favourite
Windows Logo+U+U (Turn Off Windows)
Win XP Desktop Wallpaper Changer
I love it when I find a cool picture or graphic to use as a wallpaper image. The only problem I run into is that I usually find too many pictures to use as wallpaper and can never make up my mind. So what I end up doing is changing my wallpaper constantly— I'd say I change my wallpaper on the average of once every day or two. There's still one issue I had to deal with and that was that I could really never decide on what wallpaper is my favorite and I end up flipping back and forth a lot.
Then I found a solution to my dilemma—the Windows XP Desktop Wallpaper Changer. This neat little "power toy" is a free download from Microsoft. It allows you to point to a folder full of your pictures for use as wallpaper. This means that instead of having a stagnate picture as your background Windows displays all the pictures in whatever folder you designated in a kind of really slow slide show. Sounds cool huh. Well, you haven't heard it all yet.
In addition to dynamically changing your wallpaper you can also put pictures in designated folders. The program will display these pictures as wallpaper on those days instead of your normal selection of pictures and return to your normal rotation the next calendar day. For example, I have 10 pictures chosen for my background and this is what I see everyday on my desktop wallpaper. Now let's say that I loaded a bunch of easter images in the program's designated folder for the date April 11. On April 11 when I boot my pc up the Windows wallpaper is going to see that I stored pictures within its April 11 folder and run that set of pictures (My easter images) instead of the normal set of images. When I boot up on the morning of April 12 the Wallpaper Changer will see that I have no images stored in the folder for this date and run the default set of images again.
You can set the wallpaper display length from 15 minutes to 1 week between pictures. You can manually skip a picture, or choose one image to display as long as you want . With the Windows Wallpaper changer your desktop will never be dull and lifeless again.
If you would like to download all of the wallpapers that we offer (see bottom of the newsletter) and rotate them using this program here's the simplest way to do it. First, create a folder and name it something descriptive and unique (i.e. "Worldstart Wallpaper"). From there go to our monthly wallpaper page.
Now, when the page of the graphic comes up right click the picture but don't select "Save as background", instead select "Save As" and when the window comes up asking where you want to save the picture to, select that folder we created earlier in the exercise and select save (make sure you save as a .jpg).

Once you have done that with all of the wallpaper images you want, then exit the internet and open up the Wallpaper Changer and in the "Change Wallpaper at Intervals" window navigate to the folder you dumped the wallpaper images into from Worldstart and you should almost immediately see them in the preview window. Select OK and you should see the program take affect.











